A smart chastity belt "Cellmate Chastity Cage" that can be controlled via Bluetooth from a mobile app has been targeted by hackers, and it has been remotely locked and users are told to "pay the ransom if you want it unlocked". A threat has occurred.
Hacker used ransomware to lock victims in their IoT chastity belt
https://www.bleepingcomputer.com/news/security/hacker-used-ransomware-to-lock-victims-in-their-iot-chastity-belt/
‘Your Cock Is Mine Now:’ Hacker Locks Internet-Connected Chastity Cage, Demands Ransom
https://www.vice.com/en/article/m7apnn/your-cock-is-mine-now-hacker-locks-internet-connected-chastity-cage-demands-ransom
In October 2020, Pen Test Partners, a British security company, revealed that Cellmate Chastity Cage has a security vulnerability that allows remote control by non-users.

A smart chastity belt that can lock male genitals via Bluetooth has a ``vulnerability that can be completely locked remotely by an attacker''-GIGAZINE
Pen Test Partners said in a report, ``It takes less than a few days for an attacker to steal the entire user database and use it for extortion or phishing,'' but January 2021 On the 9th, it was reported that this became a reality. The attackers launched an attack targeting the mobile app that controls Cellmate's devices, demanding a payment of 0.02 bitcoins to unlock it. According to overseas news media BleepingComputer, 0.02 bitcoin at the time of attack was equivalent to $ 270 (about 28,000 yen).
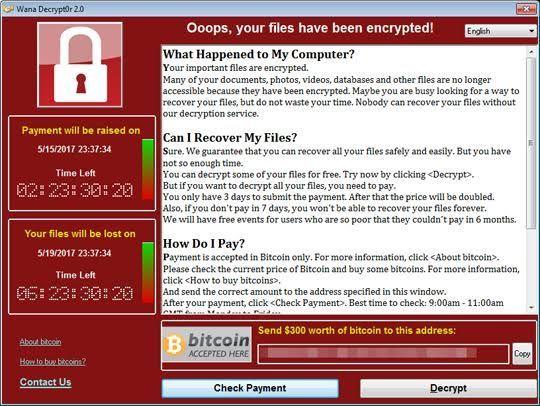
When the attack began, victims flooded in with complaints that they had lost control of their devices. In addition, it seems that some victims were sent a message saying 'Your penis is mine now'. Also, some users were concerned that ``the only way to unlock it is to disconnect the device,'' but it was possible to contact Cellmate support and request a reset, and it was possible to manually unlock the device. The manufacturer Qiui showed in a movie how to install the driver for, and the user who actually paid the ransom has not been confirmed.
Qiui, the China-based manufacturer, did not respond to requests for comment.
Qiui has reportedly fixed the vulnerability that was pointed out, so if you keep your app up to date, you won't be a target for attacks. However, such products are likely to have some vulnerabilities, so experts say, ``It will be important for all companies to have a way to contact researchers and to keep in touch with them.'' points out.
In addition, vx-underground, which collects source code and samples of malware, also publishes the source code of ransomware that was received from a person who said, "I got it from an attacker."
MalwareSourceCode/Python at main vxunderground/MalwareSourceCode GitHub
https://github.com/vxunderground/MalwareSourceCode/tree/main/Python



![Customized items for the new "Toyota Noah / Voxy" appear from Modellista [Tokyo Auto Salon 2022] [News]](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/28/2fb1fdedaad7536dd6271db30561f588_0.jpeg)
![[New Toyota Voxy (90 series)] Amplifies the characteristics of the aero body! A design that further enhances the power of the front mask! #Works direct custom deep layer 001](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/25/01568e2fbf021c0eaf7d013507c850a4_0.jpeg)
![[Toyota Noah / Voxy new model] Modellista releases various customized parts ... Actual vehicle exhibited at Tokyo Auto Salon](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/25/8268612c1e5941e62d3dfd07f8991b2f_0.jpeg)

