Finnish security company F-Secure announced on December 11, 2019 that KEYWE SMART LOCK, a smart lock developed and sold by KEYWE, Korea, is vulnerable.By abusing this vulnerability, a third party intercepts the BLE (Bluetooth Low Energy) communication between the smartphone app and the smart lock, and the door can be unlocked / locked.
"KEYWE SMART LOCK" website
F-SECURE reported vulnerabilities in KEYWE in August, and has been cooperating with verification of software patches."Keywe has never neglected security," said F-Secure representatives in the investigation.I asked the vulnerability in detail in an email interview.
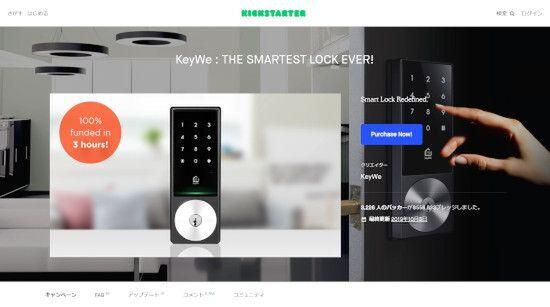
It gained popularity with crowdfunding ...
KEYWE SMART LOCK is a smart lock that Keywe is commercialized through crowdfunding such as "Kickstarter" and "Indiegogo".The feature is that you can unlock / lock in several types, such as NFC (contact with a smartphone body) and one -time password, using a special smartphone app.Kickstarter has won 3226 supporters (backers) and succeeded in raising $ 558,833 (over 60 million yen).
Kickstarter screen.The catchphrase of "Smart lock that is the best in history in history!"
"Keywe has not neglected security," said Christoph Marciniac of F-Secure Consulting, a survey member.For example, the communication between the smartphone app and the smart lock is protected by the AES 128 -bit encryption.
"However, unfortunately, the security mechanism has failed, and the security measures have been ruined."
Krzysztof Marciniak of F-Secure Consulting (Krzysztof Marciniak) in response to the mail interview
This is the flow to find vulnerabilities.First, he analyzed Keywe's smartphone app.Here he looked at the functions related to the encryption communication he discovered, hooked on a function call and looked at the message.Then, the values are generated on both the app and the smart lock (hardware), encrypted them with the common key of AES, and then replace them, and then use this value as encryption / decoding key.I decided.This is a system implemented by Keywe.
Exchange messages between smartphone apps and smart locks, and perform processing such as unlocking / locking (image is from F-Secure Labs blog).
The problem is that the common key was generated based on the Bluetooth address of the smart lock.The Bluetooth address is included in the device name and the advice packet (a radio signal informing the surrounding devices that BLE is connected is possible).On the other hand, algorithms for common keys can be determined from the analysis of the app.Therefore, if you combine the two, you can decipher the common key relatively easily.
After that, an interior device is secretly installed in the 15 -meter range from the entrance of the target (the range where BLE communication arrives), and the landlord locks / unlocks communication.All you have to do is generate a common key from the Bluetooth address obtained here, and use it to operate the smart lock.
"Tips and hardware for overcoming devices can be easily produced in Japanese yen, so it can be easily produced."
In the demo video produced by F-Secure, an attacker sneaks in by a regular user unlocked and intercepts communication with a small device.
Another problem is that the BLE pairing procedure between the smartphone and the smart lock was in the "Just Works" method without authentication.Generally, the JUST WORKS method is used in Bluetooth devices that do not have input / output devices such as headphones and mice.There are few problems with these devices, but pairing is a big problem for anyone with smart locks.This prevents the application -level authentication system, but the vulnerable mechanism mentioned above does not make sense.
Unfortunately, Marciniac says that there is no workaround to prevent attacks on Keywe SMART LOCK.In the first place, the product does not have a firmware update function, and it is impossible to renovate vulnerability.Keywe is said to make corrections from a new production lot, but he doesn't know when the release will be.At the time of writing this article, the official announcement from KEYWE has not been confirmed.
The only defensive method that the current user can do is to give up unlocking / locking with a smartphone app and return to the old physical key, or use the optional touchpad input function.
To realize a secure IoT environment
What you can see from this case is lack of recognition of development vendor security.Other security measures have been overlooked, although the encryption technology for communication is adopted, but the mechanism to generate the original encryption key is weak.Even from the “what is a unique key exchange system”, the wrong recognition is that if you protect the communication with a strong encryption method, the measures are perfect.
BLE has been fixing vulnerabilities such as pairing methods, encryption communications, and authentication methods every time the version goes up, making it strong.At least version 4.After 2 (2014), various enhancements have been enhanced, such as a secure connection method that combines a more powerful public key encryption method and a certification, and a mode that does not advertise the address of the device.If they were able to make good use of them, Keywe SMART LOCK may have not had to be a "smart lock".
That said, no matter how much the IoT device side ensures safety in the latest version, the user's smartphone side does not necessarily support it.There is also a decision to adopt an old version vulnerable method to get more users to use.
"In addition, no matter how hard you work and strengthen security, sadly, it is not directly linked to product sales."Merciniac says that startups and ventures, who have a small budget and don't want to spend much time, may make a difficult decision to prioritize "fruit" over security.
"Still, I don't want you to compromise with security."That is Merciniac's appeal.Even if you support old = vulnerable versions, secure operation is possible by identifying and taking measures assumed from the design stage, and continuously working on patch corrections and updates after the release of the product.
"Security measures are more cautious and complicated. We are experts who can support it. I want you to rely more."



![Customized items for the new "Toyota Noah / Voxy" appear from Modellista [Tokyo Auto Salon 2022] [News]](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/28/2fb1fdedaad7536dd6271db30561f588_0.jpeg)
![[New Toyota Voxy (90 series)] Amplifies the characteristics of the aero body! A design that further enhances the power of the front mask! #Works direct custom deep layer 001](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/25/01568e2fbf021c0eaf7d013507c850a4_0.jpeg)

![[Toyota Noah / Voxy new model] Modellista releases various customized parts ... Actual vehicle exhibited at Tokyo Auto Salon](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/25/8268612c1e5941e62d3dfd07f8991b2f_0.jpeg)
