Here's My Content
A new backdoor infection called "DoublePulsar" has been reported in the issue of hacking tools at the US National Security Bureau (NSA).Although the size of the infection depends on the observation, it seems that it can reach tens of thousands to hundreds of thousands.
In this issue, on April 14, US time, Shadow Brokers released many hacking tools based on the development of NSA.Several tools showed that Windows vulnerabilities were abused, and Microsoft responded in the update program.Shadow Brokers also released a vulnerability verification tool called "FUZZBUNCH".
Microsoftが対処した攻撃コードAccording to a group of security researchers surveyed about FUZZBUNCH, DoublePulsar plays a backdoor to download any script on a hacking tool.Hacking tools and DoublePulsar's terminals are at risk of executing any code through the remote control of the attacker.
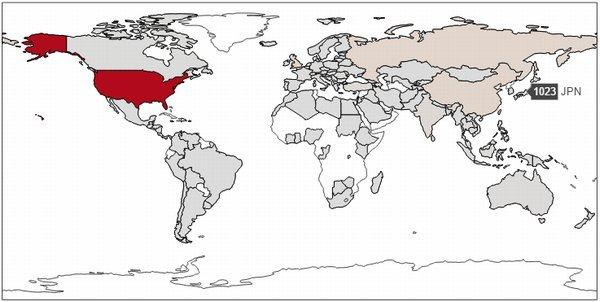
The US Security Vendor Below0day scanned more than 5.5 million units on the Internet on the Internet on April 18, discovering 3626 hosts suspected of DoublePulsar infection.The number of observations on the 21st has increased to 56,586 units.In the infected area, more than 10,000 USA and Asian countries are scattered in Europe and Asian countries, and more than 1,000 units are infected in Japan.
DOUBLEPULSARの感染地域の内訳(出典:Below0Day)Meanwhile, according to Switzerland's security vendor BINARYEDGE, DoublePulsar's infections have risen to 106,410 units as of April 21, and as of the 23rd, 164,715 units.
日本でも1000台以上が感染している可能性がある(出典:BinaryEdge)In this issue, Microsoft has dealt with the nine types of attack code that abuses vulnerabilities.Three types of attack code are not affected by Window 7 or later and Exchange 2010 or later products, but they may be affected by non -support products and recommend upgrate.
ZDNET JAPAN article is read by email every morning (free registration)
メールマガジン購読のお申し込み


![Customized items for the new "Toyota Noah / Voxy" appear from Modellista [Tokyo Auto Salon 2022] [News]](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/28/2fb1fdedaad7536dd6271db30561f588_0.jpeg)
![[New Toyota Voxy (90 series)] Amplifies the characteristics of the aero body! A design that further enhances the power of the front mask! #Works direct custom deep layer 001](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/25/01568e2fbf021c0eaf7d013507c850a4_0.jpeg)

![[Toyota Noah / Voxy new model] Modellista releases various customized parts ... Actual vehicle exhibited at Tokyo Auto Salon](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/25/8268612c1e5941e62d3dfd07f8991b2f_0.jpeg)
