On May 14th, Microsoft provided guidance to Windows users regarding the problem of frequent infections caused by ransomware "WannaCry" (also known as WannaCrypt, WannaCryptor, Wcry, etc.) in more than 100 countries around the world. published. However, if the company had responded to the recommendations issued in September 2016, it is possible that the scale of the damage would not have increased.
WannaCry threatening messages. More than 20 languages are used, including Japanese (source: Trend Micro)Microsoft released a patch to fix the "MS17-010" vulnerability in Server Message Block (SMB) v1 exploited by WannaCry in March. Delivered for Windows OS supported by security update program (including Vista whose support ended in April). Due to the damage situation, on the 13th, an unusual emergency patch was released for XP, 8, Windows Sever 2003, etc., for which support has ended.
According to information from security vendors, etc., WannaCry's infection methods include searching for SMB v1 servers exposed to the Internet and executing exploits remotely, or WannaCry located on online storage services. It seems that there is something like sending an email with a download link.
Microsoft recommended to stop using SMB v1 itself in relation to the security update "MS16-114" released in September 2016. Developed more than 30 years ago, SMB v1 asserted that it was not secure against current security threats, and that there was no benefit to continuing to use it, such as being less efficient than the latest version in terms of file sharing.
Microsoft advised against using SMB v1 in September 2016
In other words, if users had stopped using SMB v1 when this advisory was issued, it is possible that the damage caused by WannaCry would not have spread. Even if it is difficult to respond immediately after the recommendation, there is a time lag of about half a year until the end of April, when the WannaCry attack campaign seems to have started, so it can be said that there was enough time to consider the verification of alternative measures.
Workarounds and Potential Recovery
The best way to avoid a WannaCry infection is to apply the latest security updates to your computer to eliminate vulnerabilities and keep your security software up to date. It is possible to detect malicious programs such as WannaCry as much as possible.
You can also open the "Turn Windows features on or off" menu from the Windows settings "Programs and Features" and uncheck "SMB 1.0/CIFS file sharing support".
In addition, as a countermeasure against ransomware, not just WannaCry, it is necessary to frequently back up system and user data during normal times, and prepare procedures, etc., so that they can be restored in the event of an emergency. .
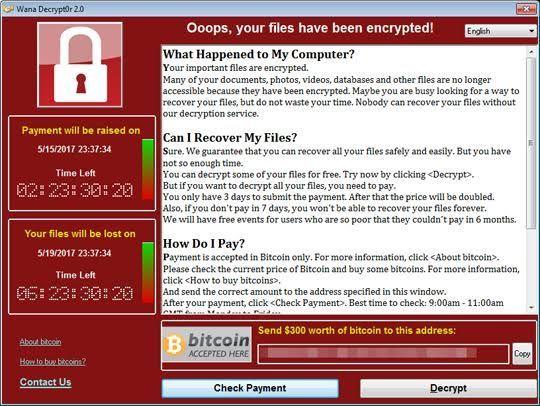
According to Symantec, the support desk in Japan has received several inquiries at this time. Although it is currently impossible to decrypt WannaCry-encrypted files, Symantec and Trend Micro are currently conducting analysis, including whether or not there is a decryption method.
In late April, it was discovered that the vulnerability exploited by WannaCry was also being exploited to infect a backdoor called "DOUBLEPULSAR". According to some reports, DOUBLEPULSAR may be used to infect WannaCry, and it seems necessary to pay attention not only to WannaCry but also to DOUBLEPULSAR when detecting and exterminating.



![Customized items for the new "Toyota Noah / Voxy" appear from Modellista [Tokyo Auto Salon 2022] [News]](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/28/2fb1fdedaad7536dd6271db30561f588_0.jpeg)
![[New Toyota Voxy (90 series)] Amplifies the characteristics of the aero body! A design that further enhances the power of the front mask! #Works direct custom deep layer 001](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/25/01568e2fbf021c0eaf7d013507c850a4_0.jpeg)
![[Toyota Noah / Voxy new model] Modellista releases various customized parts ... Actual vehicle exhibited at Tokyo Auto Salon](https://website-google-hk.oss-cn-hongkong.aliyuncs.com/drawing/article_results_9/2022/3/25/8268612c1e5941e62d3dfd07f8991b2f_0.jpeg)

